Blocking Malicious content from your network

Introduction
Did you know that nearly 30,000 websites are hacked every day? In an era where cyber threats are constantly evolving, protecting your network from malicious content more crucial than ever.
In this guide we'll explore how to configure a firewall policy on the FortiGate to block known phishing servers, malicious servers, bot nets and other threats. Using FortiGuard subscription service, we get an up-to-date scan of all these threats, grouped in an Internet service for easy deployment to our Firewall rules.
Understanding Malicious Content
Malicious content refers to any data or code that is designed to harm your network, steal sensitive information, or disrupt services.
- Malware: Malicious software designed to harm or exploit any programmable device, service, or network.
WannaCry ransomware attack
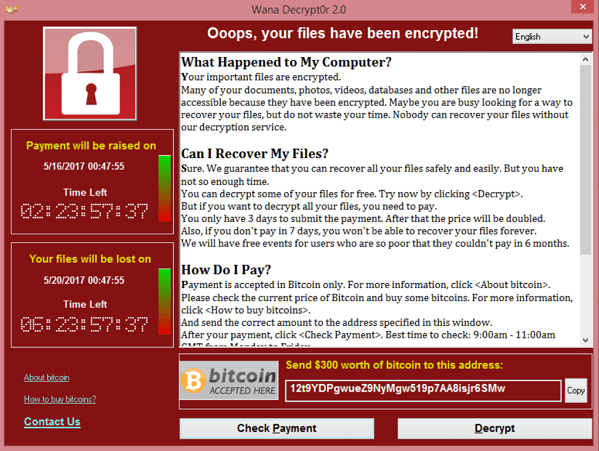
Back in 2017 the WannaCry ransomware targeted computers running Microsoft, by encrypting data and demanding ransom payments. It was a spin off a known virus called Eternal blue, which used an exploit in Server Message Block (SMB) Protocol in the Windows operating system.
- Phishing: A method of trying to gather personal information using deceptive emailed and websites.
Evaldas Rimasausskas

Between 2013 and 2015 Evaldas Rimasauskas, impersonated as a Google executive and sent phishing emails to employees at Google and Facebook. The emails appeared to be legitimate requests for payments, and as a result, Rimasauskas managed to scam the two companies out of $100 million.
- Denial-of-service (DOS) and Distributed Denial-of-service (DDoS) Attacks: Overwhelming a system's resources to render it unavailable to users.
Mirai
In 2016, Dyn, a major DNS provider, fell victim to a DDoS attack that created a widespread disruption of popular websites such as Twitter, Netflix and Reddit. The attack was carried out using a botnet called Mirai, which consisted of numerous compromised IoT devices.
If you're interested in learning more about Malicious content, I'd recommend keeping up to date with The Hacker News for what's going on in the would in Cybersecurity.
Firewall Policy Setup
We can go to Policy & Objects > Firewall Policy > Create New
- Name: I will be naming this Block Malicious Content
- Incoming Interface: LAN Interface (I want the FortiGate to monitor my internal LAN network)
- Outgoing Interface: Wan Interface (I want the FortiGate to block the malicious content from the Wan)
- Source: My LAN Subnet range group object.
- Destination: Adding internet services, Phishing services, botnets, malicious servers, tor nodes
- Action: Deny
- Log Violation Traffic: Enable
It should something like this in the end:

Okay, so let's go into a bit of detail about these internet services that we have added.
- Botnet-C&C.Server:
- A centralized computer that manages a network of compromised computers, known as a botnet.
- Malicious-Malicious.Server
- A server that hosts or distributes malicious content, such as malware, phishing sites.
- Phishing-Phishing.Server
- Known IP addresses that have hosted phishing websites.
- Tor-Relay.Node
- A server that participates in the Tor network by relaying encrypted traffic between users and the destination websites.
If we hover over Malicious-Malicious.Server we can see that it has a Total IP of 227,201 in its group. This is updated with FortiGuard subscription provided by FortiGate.
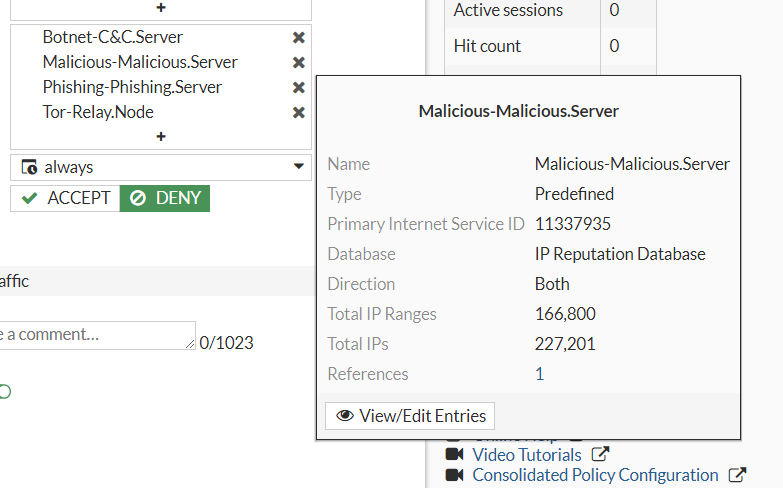
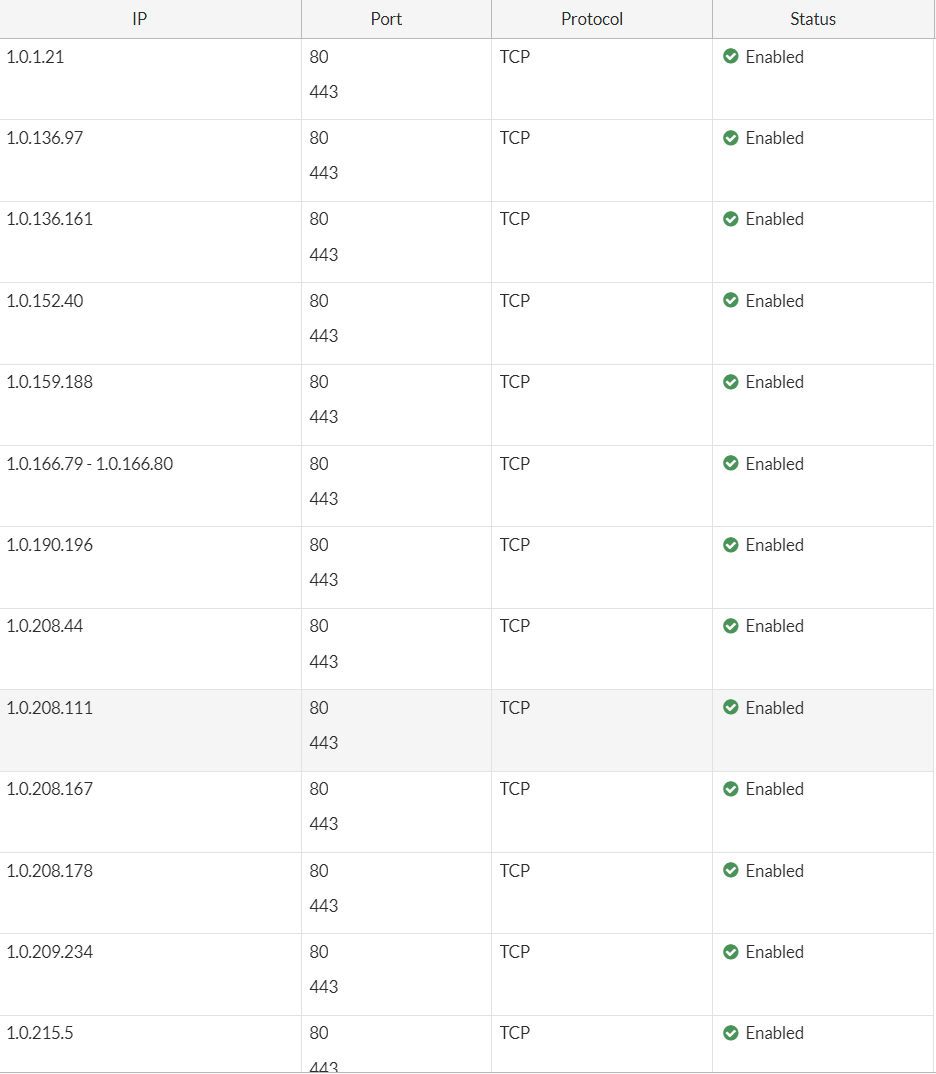
If we click the View/Edit Entries, we can see all the IP addresses on the side
We can press OK to save the firewall Policy
Firewall Policy Hierarchy
A firewall is designed to deny traffic by default. It's up to us to add firewall policies to allow traffic to specific interfaces, while adding objects and services to be permitted by the rule we create.
FortiGate firewall rule work from top to bottom. This means that the order of the rules are crucial. For the rule we have created, we want it to be above our main LAN to WAN rule so that it inspects the traffic for any of the internet services we have added and blocks the traffic ID it matches.
It should look something like this:
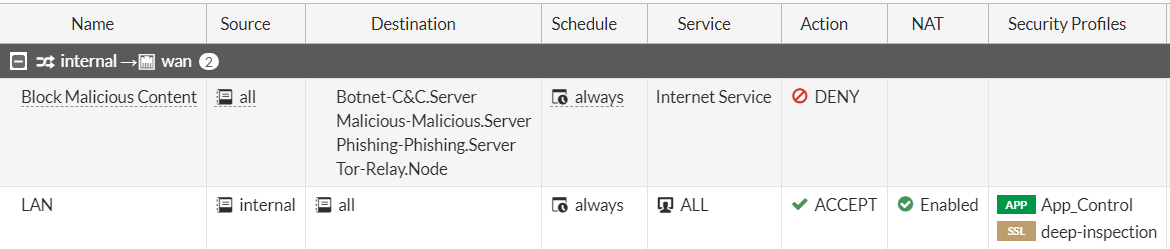
This firewall policy to Block Malicious Content will deny any traffic that matches the destination IP addresses in those specified internet services.
Conclusion
In conclusion, protecting your network from malicious content is essential in today's digital age, where cyber threats are constantly evolving. By configuring a firewall policy on the FortiGate, you can effectively block known phishing servers, malicious servers, botnets, and other threats. Utilizing the FortiGuard subscription services ensures that your firewall rules are always up-to-date with the latest threats, providing robust security for your network.
I hope you enjoyed this guide and Happy Networking!