FortiGate Firewall Policies: Simplified Setup and Actions

What Are Firewall Policies, and Why Are They Important?
Imagine your network is like an exclusive nightclub, and you want to ensure only the right people get in while keeping troublemakers out. This is where firewall policies come in - acting as the rules your bouncer follows to decide who enters and who get denied
Firewall policies are at the core of any network's security. They define how data traffic flows in and out of your network, ensuring only authorized connections are allowed. Without these policies, your network could be left wide open, exposing it to unauthorized access, malicious attacks, or inefficient resource use.
The Bouncer Analogy
To make it simpler, think of a firewall policy like the instructions you give to the bouncer at your club:
- Who's allowed (Source Rules): Just like the bouncer checks IDs at the door, your firewall checks where the traffic is coming from. Is it from a trusted device inside your network, or an unknown source from the internet?
- Where Are They Going? (Destination Rules): the bouncer also considers where the guest is headed. Is it a public dance floor (general internet access) or the VIP lounge (a sensitive server)? Your firewall ensures traffic is heading to an approved destination.
- What Are They Doing? (Service Rules): The bouncer ensures guests are dressed appropriately for the event - your firewall does the same by checking if the traffic is using permitted services or protocols, like web browsing (HTTP.HTTPS) or file sharing (FTP).
- Trouble Checks (Security Features): Even if someone meets the entry criteria, the bouncer can deny access if they look suspicious. Similarly, your firewall can block traffic that seems malicious using features like intrusion prevention or application control.
Setting Up Firewall Policies in FortiGate
In this section, you'll learn how to set up effective firewall policies in FortiGate to protect your network, using clear instructions and relatable examples.
If we log on to our Firewall and go to Policy and Objects > Firewall Policy, we can see all of our Firewall policies that we have set up.
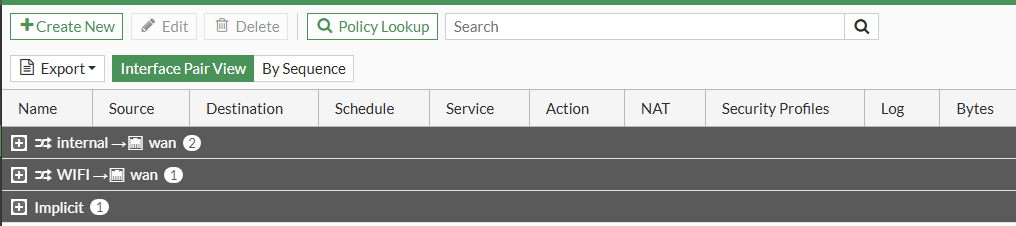
If this is a new device, then it will most likely be empty.
Creating a LAN to WAN Policy
For internet connection to the LAN network, we will need to set up a Firewall policy that has our Incoming interface be the LAN network and the outgoing interface be the WAN.
If we create new in the policy at the top, we can go into detail on each option when creating a new policy.
- Name: You want to name the policy suitable to what it's doing. I.E "LAN > WAN"
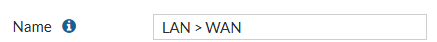
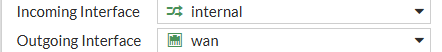
- Incoming Interface: We know this is coming into the LAN
- Outgoing Interface: We know this is coming out of the WAN
- Source: I would put this as the subnet range of the LAN, just like in are bouncer analogy, this is where the traffic is coming from.

- Service: All - However you may want to specify what services you want, like HTTP, HTTPS, SMTP etc.
- Action - Accept. This is to accept the rule or Deny, block the rule.

- Inspection Mode: Flow-Based. It inspects and analyses traffic as it passes through the FortiGate device without fully reconstructing the session memory.
- Proxy-based: Proxy-based inspection works by temporarily holding traffic (packets) and analysing it deeply before allowing or denying it
- NAT - Enabled. This translates private IP addresses used on our local network into public addresses used on the internet.
- Security Profiles: At the moment I will keep these blank. However, security Profiles are incredibly powerful. You have the option to set up Anti Virus, Web filtering, DNS Filter, Application Control, IPS, Certificate inspection or even Deep Certificate Inspection. These profiles can be set up to except, block and monitor and analyse the traffic passing through the rule.
You can create customized profiles to block certain URLs, block applications like YouTube, gambling applications, social media applications and so much more.
IPS (intrusion preventions sensor) can be setup to block and monitor malicious malware, known vulnerabilities or reconnaissance scans to the network.
- Logging Options: - All sessions, this will log all traffic going through this firewall for monitoring purposes.
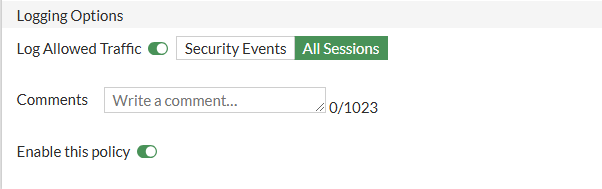
Once the policy is completed, we can click OK at the bottom.
Setting Up a Block Policy
We can create policies to block certain traffic that we don't want running on our policy.
For this example, I will block HTTP and HTTPS running on IP address 192.168.10.8 on my LAN to WAN network.
We can use this scenario in the sense that we don't want this machine access to the internet via HTTP or HTTPS,
This could be useful for isolating a misbehaving device, enforcing internet restrictions on a specific machine, or testing traffic restrictions for troubleshooting purposes.
We need to add the IP address as an object
Go to Policy and Objects > Addresses Create New
- Name: Block-Device - 192.168.10.8
- IP/Netmask: 192.168.10.8/32
- Interface:
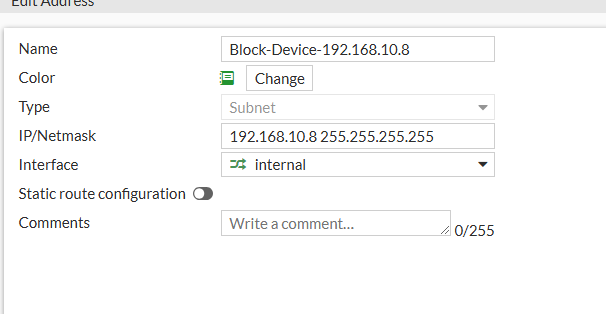
We can press OK to save the address.
Go to Policy & Objects > Firewall Policy > Create New
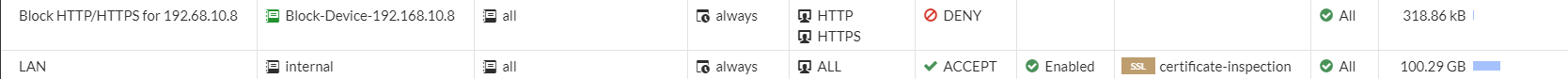
- Name: Block HTTP/HTTPS for 192.168.10.8
- Incoming Interface: LAN
- Outgoing Interface: WAN
- Source: Block-Device-192.168.10.8
- Destination: All
- Service: HTTP, HTTPS
- Action: Deny
- Log Violation Traffic: Enable

We can press OK to save the Policy.
We will need to make sure our block policy is above our LAN-Wan policy.
Testing Policy
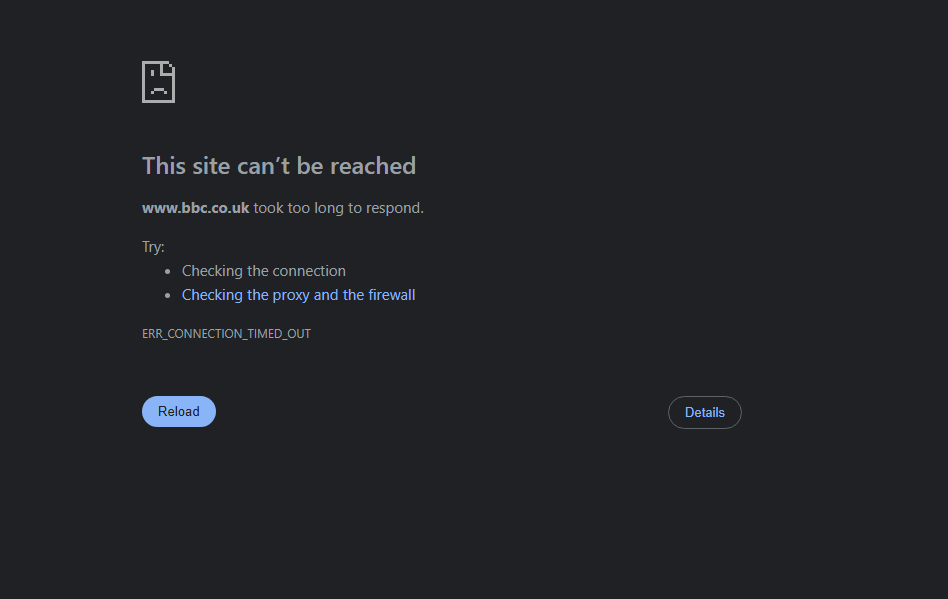
We can configure our PC to use the IP address of 192.168.10.8 as a static IP address. Then we can test if HTTP and HTTP is being blocked.
If I navigate to www.bbc.co.uk, we can see that we are not able to access the website.
We can also check the logs on the FortiGate by going to Log & Report > Forward Traffic.
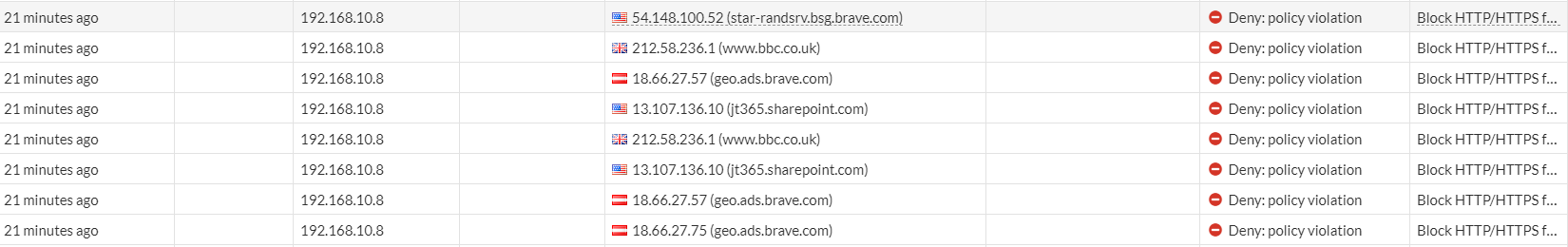
We can see from the logs that our firewall policy is working as attended. It is not allowing 192.168.10.8 to access the internet via HTTP or HTTPS.
If we click on one of these results, we will get more from the details section.
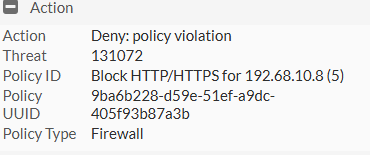
We can see from the action section, that it has hit the deny: policy violation with the policy ID information.
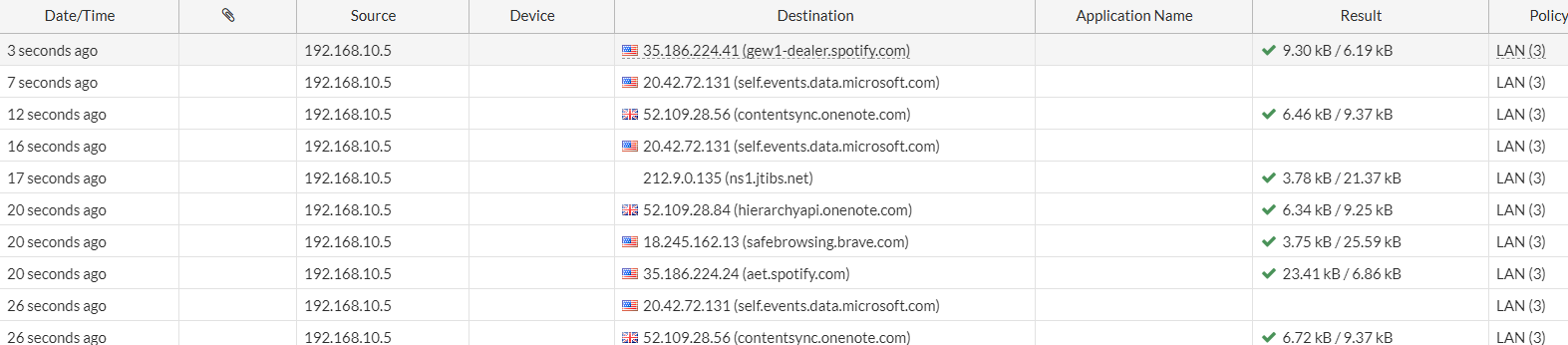
However, if we look at another IP address on the LAN, we can see that traffic is passing through as attended to do so.
Blocking Applications and Websites
We can also block websites and applications using the security profiles and adding them to a Firewall policy.
For this example, we will use the same IP address 192.168.10.8 to block the website Twitter or (x.com) via URL blocking and YouTube via application blocking.
Web Filter
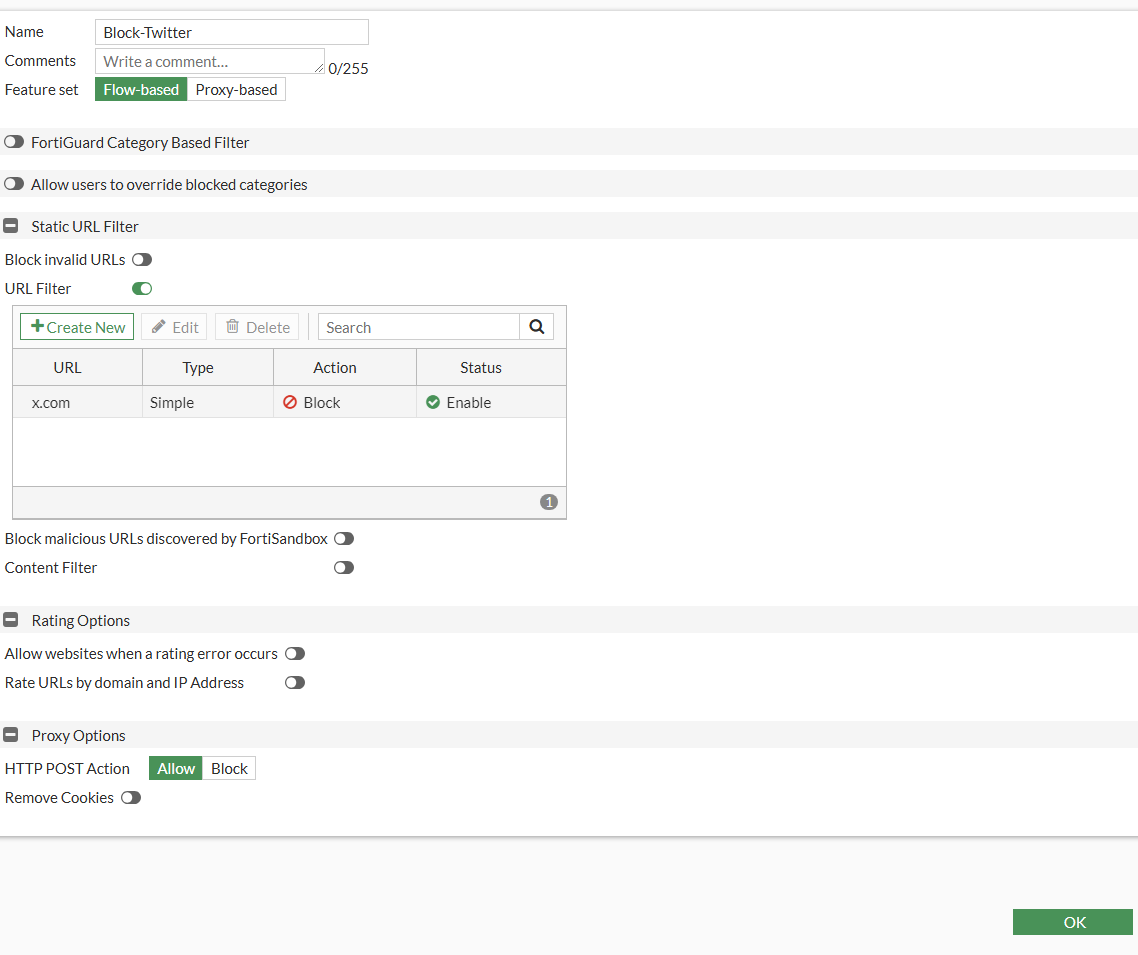
We can go to Security Profiles > Web Filter > Create New
- Name: Block Twitter
- URL Filter: Enable
Click create new on the window to block twitter.
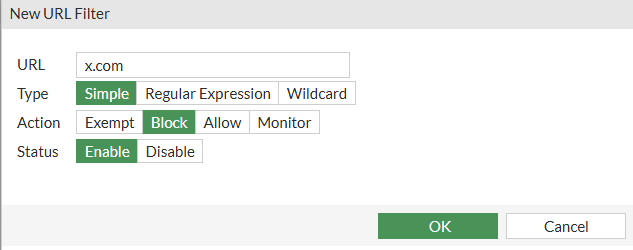
We can click OK to save it
Application Control
Go to Security Profiles > Application Control
- Name: App_Control
Press Create New.
We can type in the search bar YouTube and see the results
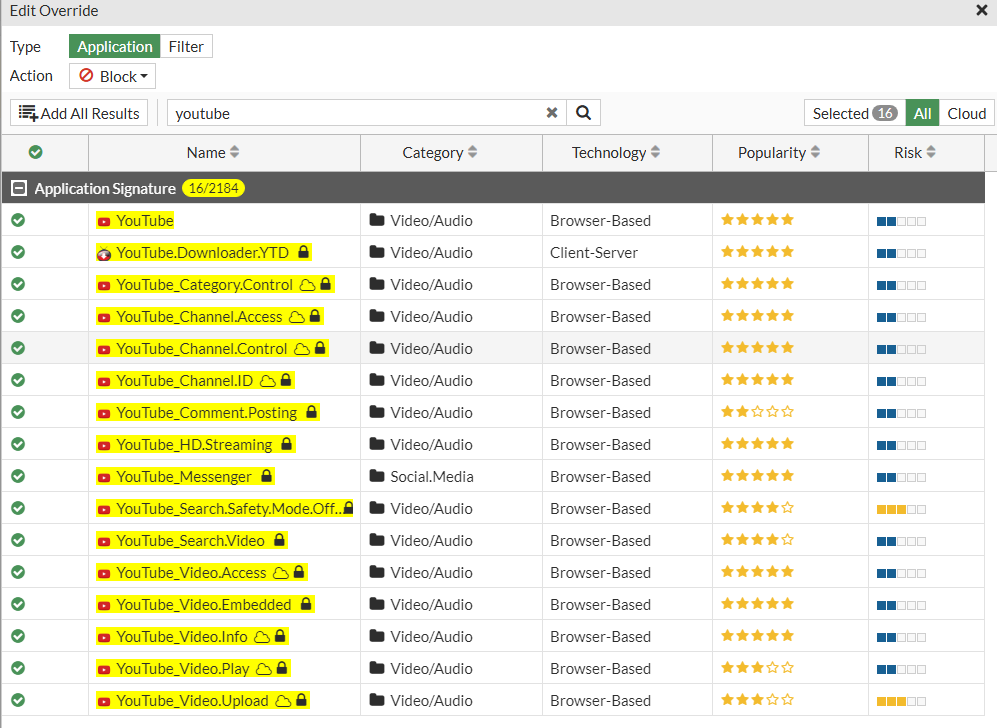
We can select all of these and press Add Selected to add these in to our new App_Contol.
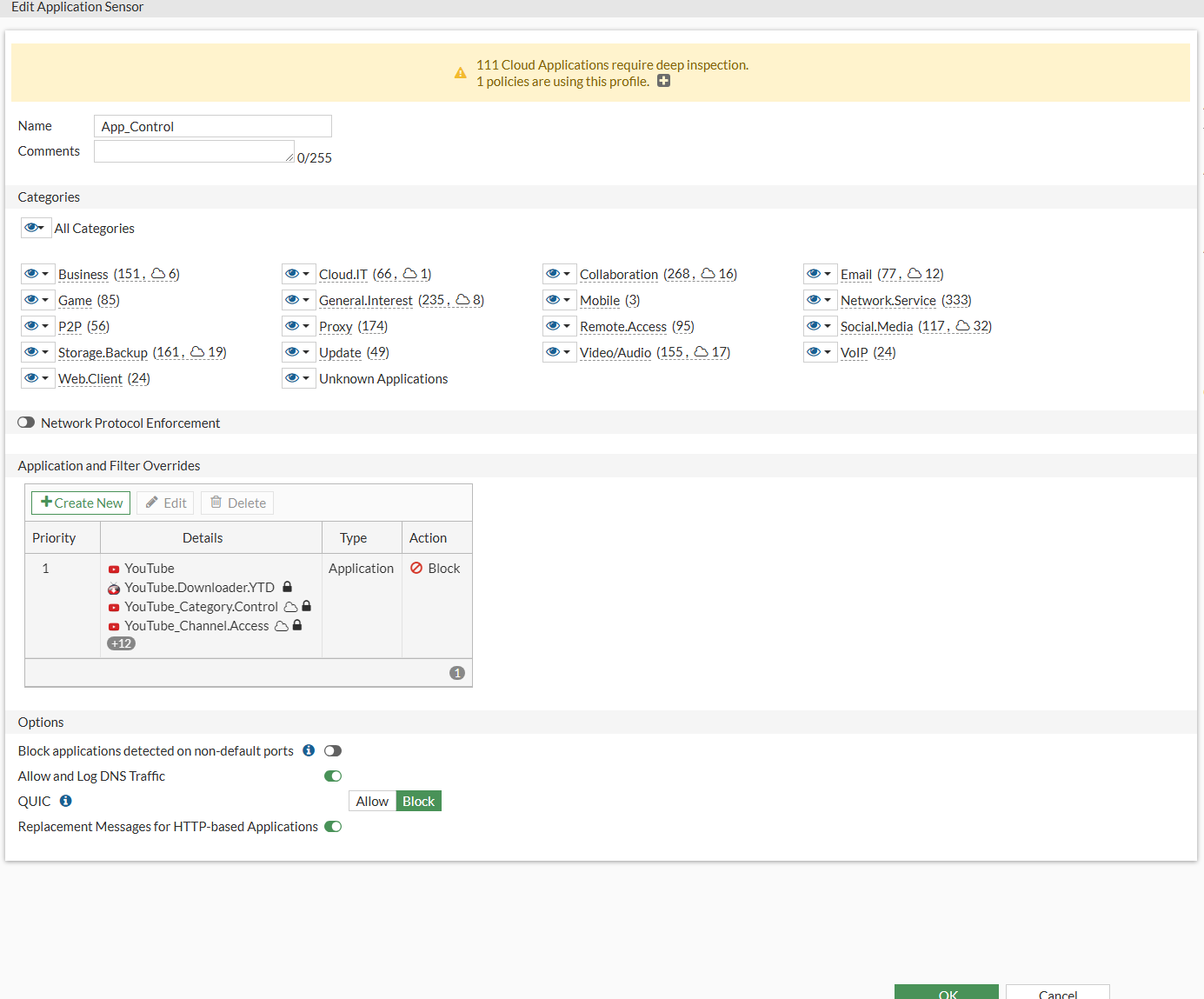
Press OK to save the option.
Firewall Policy setup
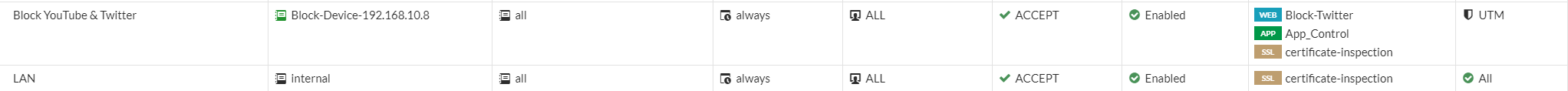
Go to Policy & Objects > Firewall Policy > Create New
- Name: Block YouTube & Twitter
- Incoming interface: LAN
- Outgoing interface: WAN
- Source: Block-Device-192.168.10.8
- Destination: All
- Service: ALL
- Action: Accept
- Inspection Mode: Flow-based
- NAT: Enabled
- Web Filter: Block-Twitter
- Application Control: App_Control
- SSL Inspection: Certificate-inspection
- Log Allowed Traffic: Security events
Press OK
Testing Web Filter and Application Control
If we try and go to https://x.com or https://youtube.com on 192.168.10.8, we will not be able to access these sites.
We can also check the FortiGate logs in Web filtering and Application Control to see that it is getting blocked.
Go to Logs & Report > Web Filter
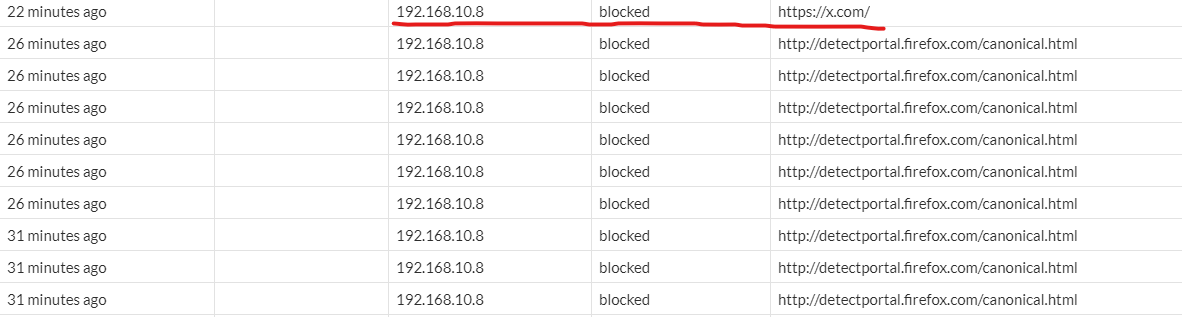
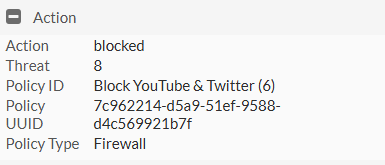
Go to Logs & Report > Application Control
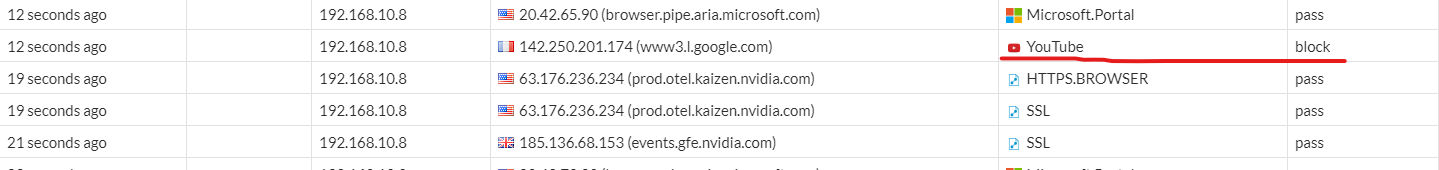
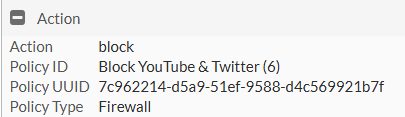
We can see by the logs that these sites are being blocked for this IP address.
Conclusion
Firewall policies are the backbone of any secure network, providing control over how data flows and ensuring only authorized traffic is allowed. With FortiGate, you have access to powerful tools like Security Profiles, Web Filtering, and Application Control, allowing you to manage network traffic with precision.
In this guide, we've demonstrated:
- How to create essential LAN-to-WAN policies for internet access.
- How to block traffic for specific devices using IP address-based policies.
- How to enhance your policies with advanced Web Filtering and Application Control to block specific websites and applications like YouTube and Twitter.
- The importance of testing and logs to validate your configuration.
Whether you're securing your home network, isolating misbehaving devices, or enforcing corporate policies, these steps highlight the flexibility and power of FortiGate firewalls.
I hope this guide has helped, and Happy Networking!